Do you hate insecure base images? Sure, we all do..
I built a thing: secure-base-images. It’s a minimal, security-hardened Docker base image for static Go binaries.
Issue
Most Docker images are bloated. They include shells, package managers, and a ton of dependencies you don’t need. This creates a huge attack surface that your security team loves to talk about, and drives fast pipeline guys like me insane. For static Go tools, you literally just need the binary and some certs.
Solution
A distroless base image that gives you:
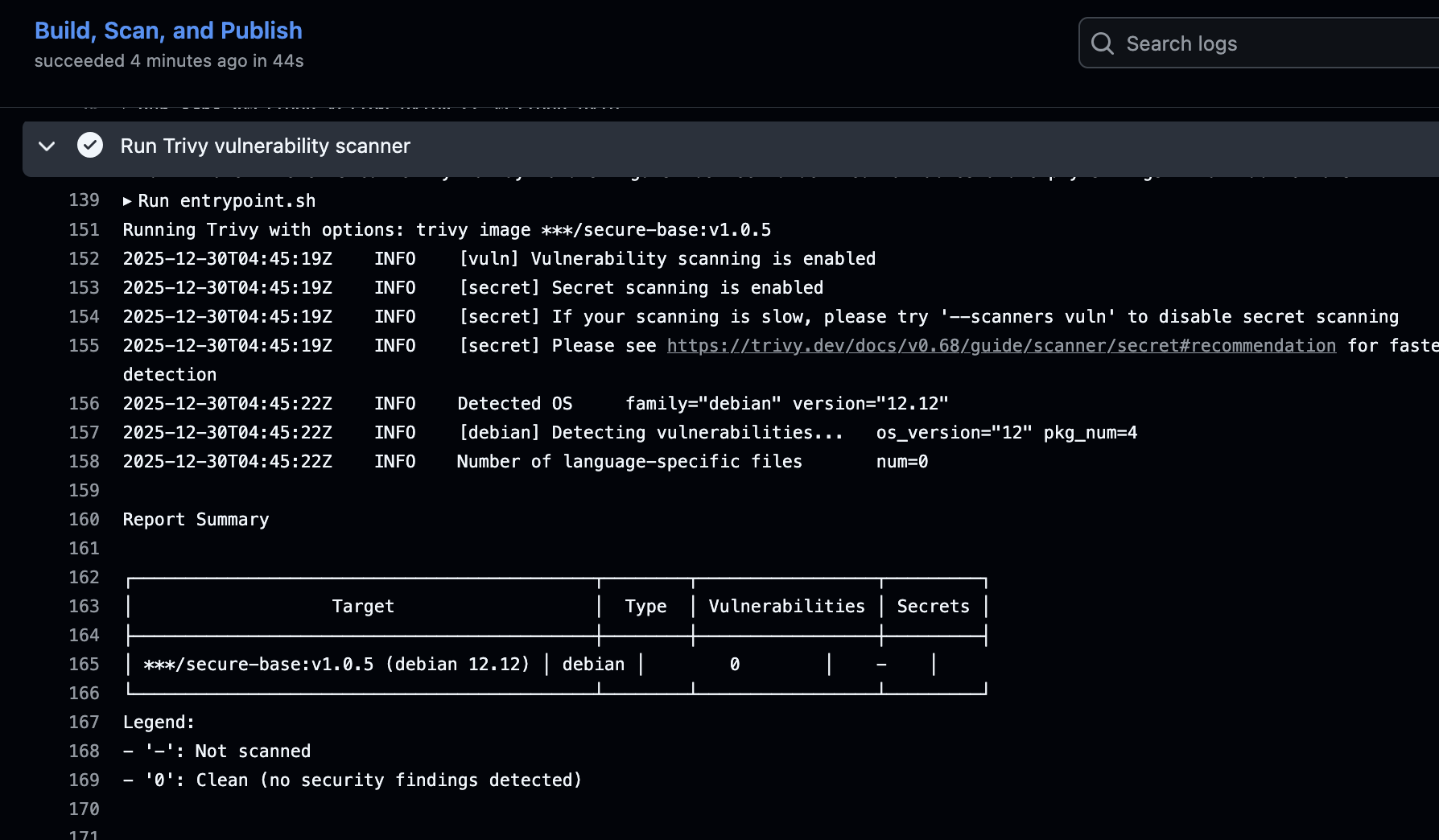
- Zero vulnerabilities - Automated Trivy security scanning catches CRITICAL/HIGH issues
- Minimal attack surface - No shell, no package manager, just your binary
- Non-root execution - Runs as uid 65532 by default
- Fast builds - Multi-platform support (amd64/arm64) via GitHub Actions
- Dead simple - 3 lines in ya Dockerfile
Usage
FROM swantron/secure-base:latest
COPY myapp /app
ENTRYPOINT ["/app"]
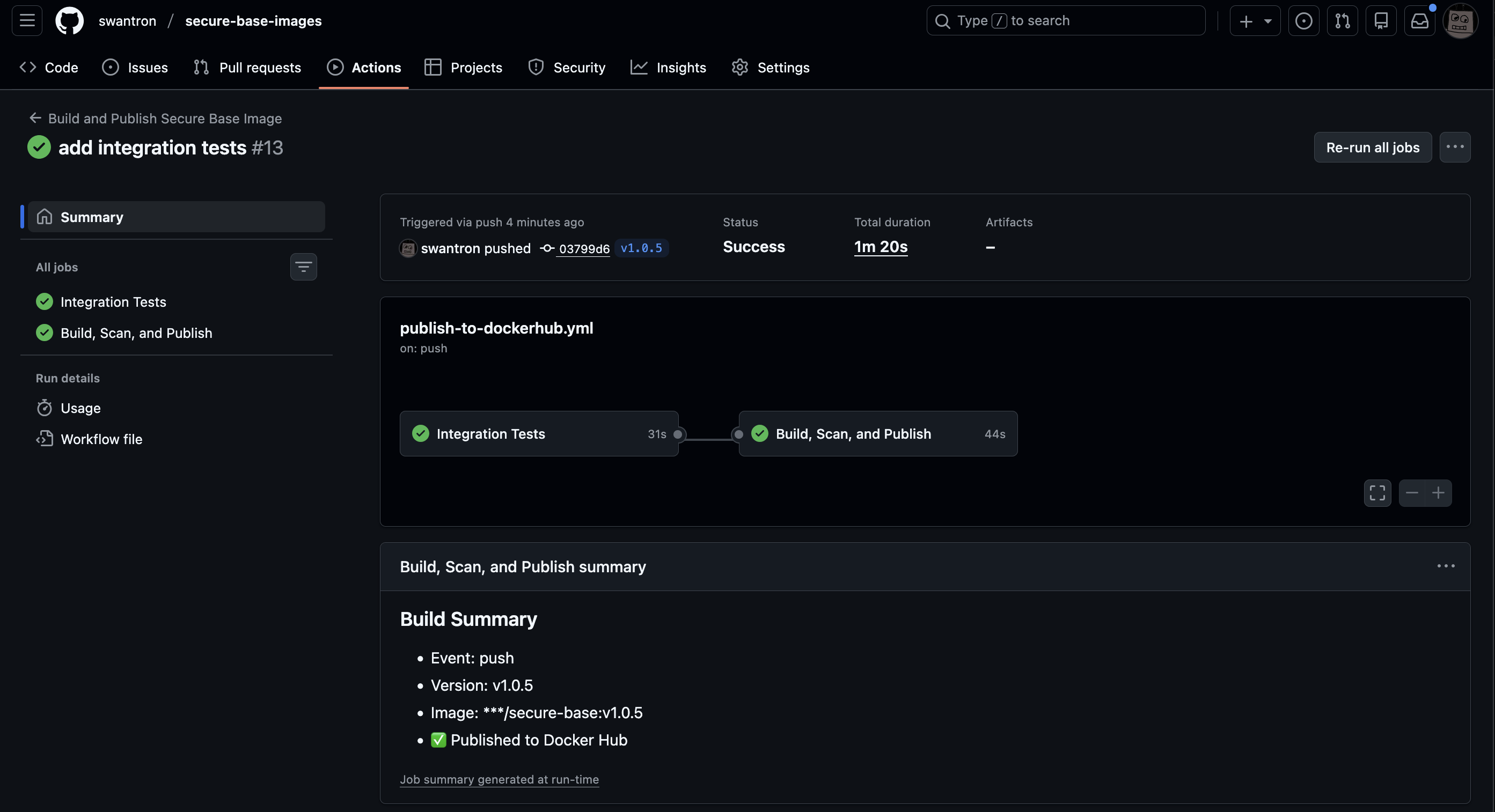
That’s it. Push a tag, GitHub Actions builds it, scans it with Trivy, and publishes to Docker Hub if it’s clean (it is.)
Under the Hood
The GitHub Actions workflow is doing the heavy lifting:
- Runs integration tests (non-root user, no shell, CA certs present, etc.)
- Builds the image
- Scans with Trivy - build fails if vulnerabilities found
- Multi-platform build (amd64/arm64)
- Pushes to Docker Hub on release tags
It’s opinionated but in a good way. Security by default.
Get It
Source: https://github.com/swantron/secure-base-images
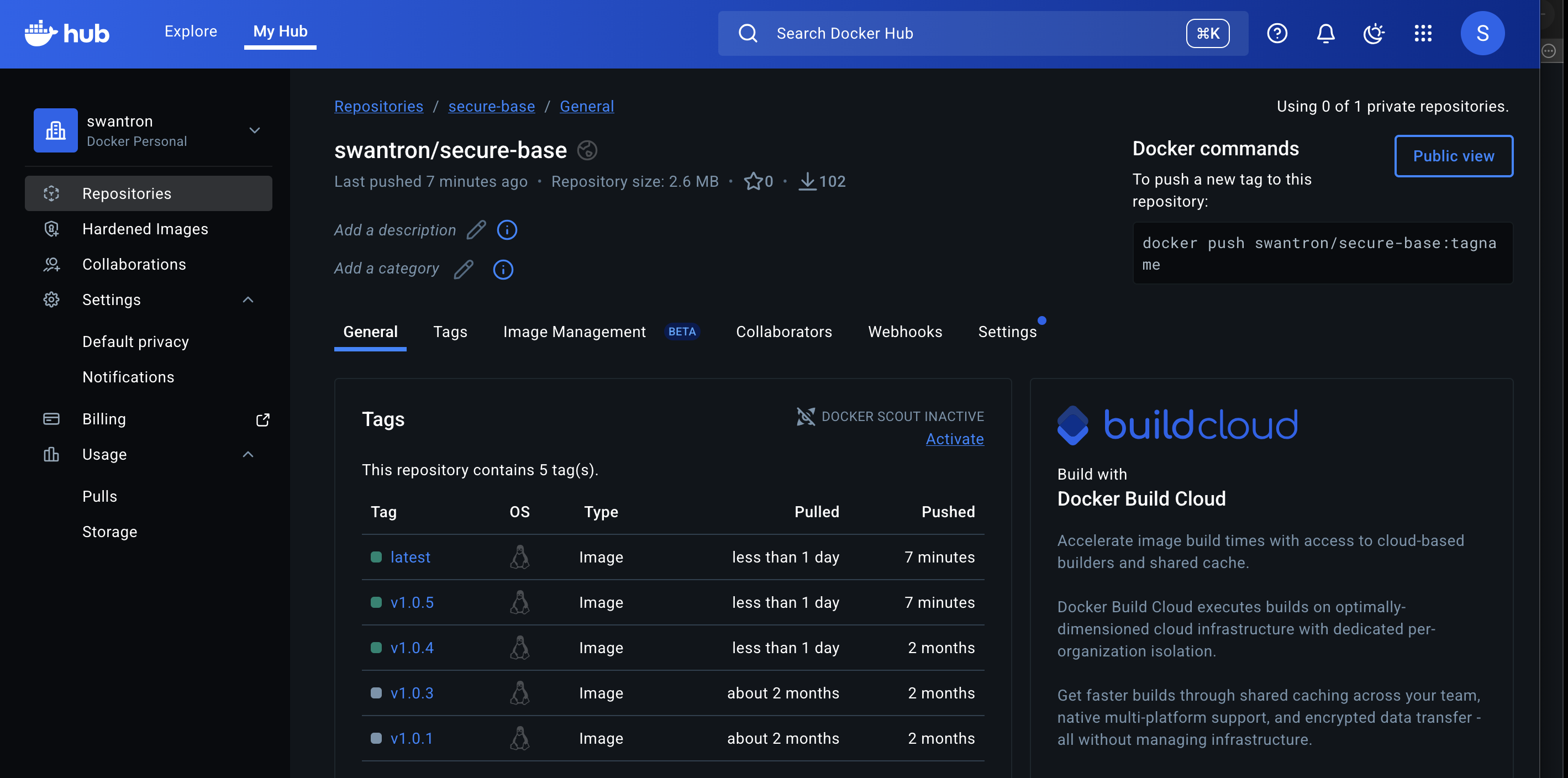
Docker Hub: swantron/secure-base:latest
The QUICKSTART.md gets you from zero to published in about 10 minutes.